OIDC Support
Aptos Keyless supports the following IdPs on our network(s). Support for additional IdPs to come. Please reach out if you have need for coverage for a specific use case.
| Identity Provider | Devnet | Testnet | Mainnet |
|---|---|---|---|
| Live | Live | Live | |
| Apple | Live | Live | - |
| Microsoft | In review | - | - |
| Github | In review | - | - |
| In review | - | - |
To integrate Aptos Keyless into your dApp, you must register your dApp with at least one of the available identity providers via their OIDC registration process. Each respective registration process will assign a Client ID to your application, which will serve as an identifier for your application in the Keyless architecture.
Registering your dApp with Google
Step 1: Sign in to Google Developer Console
- Navigate to the Google Cloud Console.
- Sign in with your Google account credentials.
Step 2: Create a New Project
- If you don't have an existing project, click on the "Select a project" dropdown menu at the top of the page and choose "New Project."
- Enter a name for your project and click "Create." Detailed instructions can be found here.
Step 3: Configure Consent Screen
- In the left sidebar, navigate to "APIs & Services" > "OAuth consent screen."
- Choose "External" user type and click "Create."
- Enter the required details such as the application name, user support email, and developer contact information.
- Optionally, add additional details like the application logo and privacy policy URL.
- Click "Save and continue." Detailed steps are available here.
Step 4: Register Your Application
-
In the left sidebar, navigate to "APIs & Services" > "Credentials."
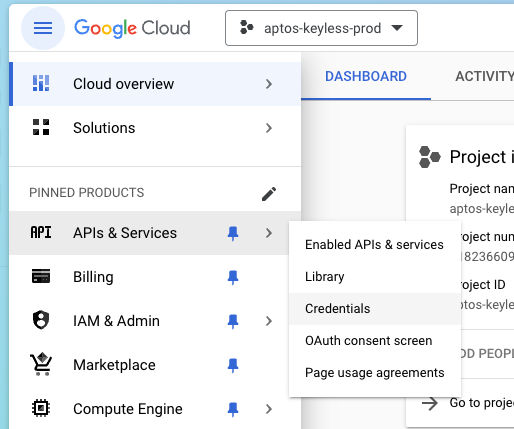
-
Click on "Create Credentials" and select "OAuth client ID."
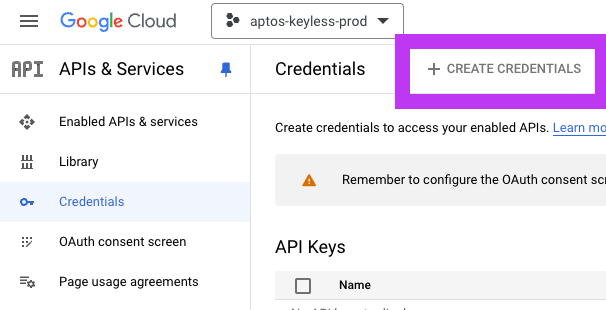
-
Choose the application type (e.g., Web application, Desktop app, or Mobile app).
-
Enter the necessary details such as the name of your application and the authorized redirect URIs. For OIDC, the redirect URIs should follow the format https://your-app-domain.com/auth/google/callback.
-
Click "Create."
Step 5: Obtain Client ID and Client Secret
- After creating the OAuth client ID, Google will provide you with a client ID and client secret. These credentials are essential for authenticating your application.
- Note down the client ID and client secret securely. Do not expose them publicly.
Step 6: Configure OIDC Integration in Your Application
- Integrate OIDC authentication into your application using a suitable OIDC library or framework (e.g., Passport.js for Node.js, Spring Security for Java, or Auth0 for various platforms).
- Use the client ID and client secret obtained from Google to configure OIDC authentication in your application settings.
- Set up the appropriate callback URL (https://your-app-domain.com/auth/google/callback) for handling authentication responses from Google.
Registering your dApp with Apple
Step 1: Sign in to Apple Developer Account
- Go to the Apple Developer website.
- Sign in with your Apple ID.
- Enroll in the Apple Developer Program if not already.
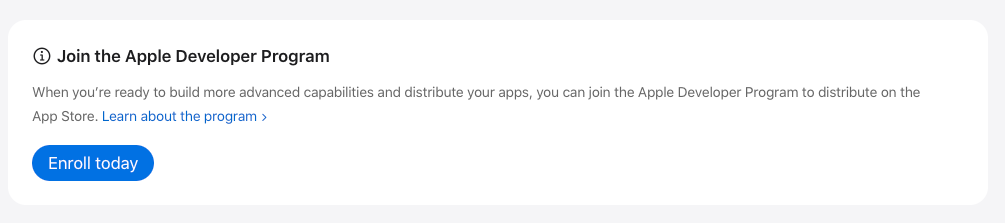
Step 2: Create a New App ID
- Navigate to the "Certificates, Identifiers & Profiles" section.
- Click on "Identifiers" in the sidebar.
- Click the "+" button to create a new App ID.
- Fill in the details for your app, including the name and bundle ID.
- Enable "Sign in with Apple" under the "Capabilities" section.
- Click "Continue" and then "Register" to create the App ID.
Step 3: Generate a Private Key
- In the "Keys" section of the "Certificates, Identifiers & Profiles" page, click the "+" button to create a new key.
- Enter a name for the key, enable the "Sign in with Apple" capability, and click "Continue."
- Download the generated private key and securely store it. This key will be used to authenticate your app with Apple's OIDC service.
Step 4: Configure Redirect URIs
- Under the "App ID" section, locate your newly created App ID and click on it.
- Scroll down to the "Sign in with Apple" section and click on "Edit."
- Add the redirect URIs that your application will use for callback after authentication. The format should be https://your-app-domain.com/auth/apple/callback.
- Click "Save" to update the settings.
Step 5: Set Up Your OIDC Integration
- Use an OIDC library or framework compatible with Apple's OIDC service (e.g., Passport.js for Node.js, Spring Security for Java).
- Configure your application to use the client ID and private key obtained from Apple during the registration process.
- Set up the appropriate callback URL (https://your-app-domain.com/auth/apple/callback) for handling authentication responses from Apple.